Press Release
January 17, 2022
Digital Arts Inc.
Beware, File-Sharing Services Being Used by Malware
— You can't be too careful with the official URLs for Discord and OneDrive —
Information security solutions provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; hereinafter referred to as "Digital Arts"; Securities Code 2326) is pleased to announce the release of a security report on file-sharing services exploited by malware.
File-Sharing Services Discord and OneDrive Being Used by Malware
File-sharing services are used by many companies to share large amounts of data and as an alternative to PPAP (password-protected ZIP files), but did you know that these file-sharing services are being abused by malware? The specific method of attack is to upload a file with malware to a legitimate file-sharing service, and then spread the malware infection by spreading the malicious URL via e-mail or e-mail attachment. These file-sharing services have been abused for a long time.
Based on the URLs reported by URLhaus, a project that shares malicious URLs used to distribute malware, in the four months from September 2021 to the end of December 2021, Digital Arts classified the URLs by service name (IP address format was excluded), and found that the URLs of two services, Discord and OneDrive, were being prominently exploited toward the end of 2021.
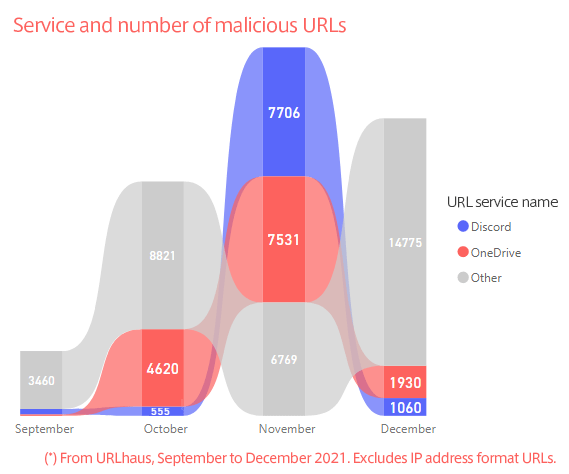
Legitimate file-sharing service Discord being misused
Discord is a free communication application. It is compatible with a variety of computer and mobile operating systems, and is widely used around the world for voice, video, and text chats not only through its dedicated application but also through web browsers. You can also share files via chat messages, and each shared file will have its own URL, which can be viewed and downloaded by anyone with the URL. However, this ability to share files via URLs like a file-sharing service has also been exploited by attackers. The URLs take the format shown below.
hxxps://cdn.discordapp[.]com/attachments/channelID/fileID/filename
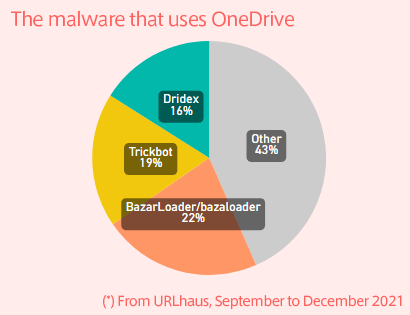
Dridex was the most common malware that tried to infect computers using Discord file-sharing URLs, accounting for more than 90% of the reported Discord URLs.

Dridex*1, which was previously discussed in a Digital Arts security report, exploited a large number of URLs of illegitimate websites. However, this time, Dridex has been using a noticeably larger number of legitimate Discord file-sharing URLs instead of illegitimate websites.
We also confirmed that it was using XLL files*2 created with Excel-DNA. Sometimes as many as 150 Discord URLs are used at a time. We have also confirmed that Dridex is being spread by spam e-mails that take advantage of popular TV shows. The e-mails invite you to watch the sequel of the show ahead of time to try and make you open the attached file. If the macro is enabled and executed after the file is opened, it will download the malware placed on Discord and lead to Dridex infecting the computer.
Exploitation of OneDrive
OneDrive is Microsoft's cloud storage service. In Windows 10 and Windows 11, OneDrive is installed by default, so it is likely that a great many people use it on a regular basis.
In the past, it was not uncommon for OneDrive to be abused, but in October, the number of cases suddenly increased. The OneDrive URL is api.onedrive.com/onedrive.live.com/files.1drv.com/1drv.ms
It uses multiple domains, all of which are legitimate.
In October 2021, international researchers found that the URLs of malicious files were surviving for days because OneDrive (Microsoft) would be slow to take action. Tech media around the world reported on this fact, shinning the spotlight on it for a moment. Since then, OneDrive has been quicker to move.
E-mail security measures that don't allow access to services not used for business through filters are also important
Discord is notable for its exploitation by Dridex, but it has also been exploited by many other attackers and malware. The same goes for OneDrive. The service provider may be taking measures to deal with exploitation, but even if the file or URL is quickly dealt with and invalidated, the attacker can simply create a new, disposable one. It is essentially a game of cat and mouse.
In recent years, the movement to abolish PPAP in Japan has gained traction, and an increasing number of organizations seem to be switching to systems that incorporate file-sharing services. You can't simply rest assured when a URL is for a legitimate service. Discord and OneDrive, which were prominently exploited, are services with a lot of private users. It is important to use URL filters to prevent access to services unnecessary for business. It is also important to take security measures such as using a mail gateway to reject unsafe e-mails in advance based on attachments and source addresses.
Digital Arts suggests controlling online storage usage with filters, whitelisting, and ZIP Encryption Circumvention
- In i-FILTER Ver. 10, it is possible to block file-sharing services.
- It can categorize services and filter by category, such as Discord (cdn.discordapp.com) as [Chat] and [VoIP], and OneDrive (api.onedrive.com/onedrive.live.com/files.1drv.com/1drv.ms) as [Online Storage]. In addition, with our Web Service Controls, you can fine-tune settings to allow for only the OneDrive services you need.
- i-FILTER Ver. 10 and m-FILTER Ver. 5's new standard of security measures — Whitelisting
- With whitelisting, you can safely open all received e-mails and access the website you want to, reducing the management load on the IT department. Digital Arts' "Whitelisting" will help bring about a more secure world.
- Is PPAP ineffective? For countering external attacks such as Emotet and IcedID, use Digital Arts' ZIP Encryption Circumvention
- PPAP has become customary in many companies and organizations in Japan when sending files via e-mail, but it poses various risks as it does not encrypt files to ensure a proper level of security. Digital Arts was quick to raise the alarm about these risks assocated with "ZIP encryption" systems, and is working to resolve them.
Click here for the report on file-sharing services being exploited by malware.
The following is available on our site.
Security Report
- *1 Security Report: Dridex - a Piece of Malware that Abuses Larger Numbers of Illegitimate Websites to Cause Infection via Email
https://www.daj.jp/security_reports/210309_1/ - *2 Security report: Attacks using unfamiliar XLL files (Excel add-ins) are on the rise
https://www.daj.jp/security_reports/211005_1/
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995, the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere.
Otemachi First Square, West Tower 14F, 1-5-1, Otemachi, Chiyoda-ku, Tokyo, Japan
URL: https://www.daj.jp/