Press Release
Novenber 17, 2017
Digital Arts Inc.
Targeted attack solution that confirms banking malware is blocked
~Collaborative solution between latest version of i-FILTER and m-FILTER blocks multiple confirmed examples such as Ursnif and DreamBot~
TOKYO, Japan (November 17, 2017) – Digital Arts Inc. (headquartered in Chiyoda-ku, Tokyo, Japan, CEO: Toshio Dogu, hereinafter referred to as “Digital Arts”, Code 2326) a leading provider of information security software, announced that measures have been taken against banking-related malwares Ursnif and DreamBot. They target internet banking with the goal of receiving illegal money transfers. To combat them, a collaboration between i-FILTER Ver. 10, which is aimed at businesses and government agencies and was released in September 2017, and e-mail security software m-FILTER Ver. 5. The two work together to form a solution to block Ursnif, DreamBot and others.
The Trojan horse malwares Ursnif and DreamBot steal bank and credit card IDs and passwords, and have been in circulation since the beginning of 2017 in Japan and made a resurgence in September of 2017. By October, much damage had been reported. The National Police Agency reports that the amount of damage in Japan exceeds 500 million yen1, and as the damage has increased, the malware has also spread even further. The Japan Cyber Crime Control Center (JC3) also released a special warning on these2.
Using Digital Arts’i-FILTER Ver. 10 in conjunction with m-FILTER Ver. 5, has been confirmed to block the above-mentioned malware3 as samples have been obtained of both were tested to confirm.
Infection methods, and how they can be blocked using i-FILTER Ver. 10 and m-FILTER Ver. 5.
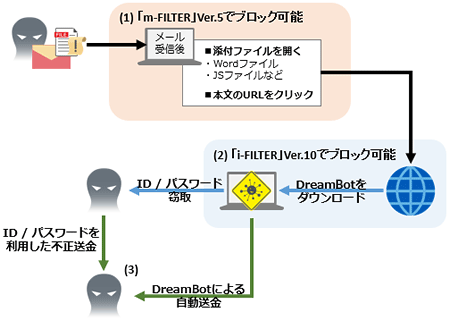
- (1)Send an Office document, URL etc. containing a macro to download DreamBot by e-mail
- ⇒ Blockable with m-FILTER Ver. 5
- (2)Click a link in the e-mail body or open the attached file, leading to a download and infection by DreamBot
- ⇒ Blockable with i-FILTER Ver.10
- (3)After infection, device is remotely operated via C&C server and “Tor” in order to steal ID and password, then automatically remit money.
Infection methods, and how they can be blocked using i-FILTER Ver. 10 and m-FILTER Ver. 5.
(in the case of DreamBot)
- Method of verification
-
Digital Arts received an e-mail containing a temporary samples of Ursnif and DreamBot via m-FILTER Ver. 5, and also launched temporary samples of Ursnif and DreamBot in i-FILTER Ver. 10.
With the targeted attack solution made possible by a collaboration between i-FILTER Ver.10 and m-FILTER Ver.5 and released in September of 2017, DreamBot’s first stage of infection (infection method 1 above), it was confirmed that only the e-mail itself or the attached file was being quarantined.
In i-FILTER Ver. 10, it was confirmed that it is blocked at the time of DreamBot’s download communication via macros and scripts attached to e-mail (infection method 2 above.)
We at Digital Arts plan to bolster defenses against increasingly complex external attacks through a combination of i-FILTER Ver. 10 and m-FILTER Ver. 5, and by obtaining specimens of various types of malware.
- Verification environment
-
- ・i-FILTER Ver. 10.00 R 01 (database at the time of delivery on September 19, 2017)
- ・m-FILTER Ver.5.00 R01
- Number of validation samples (e-mail) and blocking rate
-
- 100% block in 33 emails
- ※1 Source:National Police Agency - Regarding the threat surrounding cyberspace in the first half of 2017(PDF)
- ※2 Source:Beware of damage caused by Internet banking malware DreamBot (PDF)
- ※3 There are many variants of malware including banking malware. We do not guarantee that they will all be blocked or quarantined.
- ※ DIGITAL ARTS, i-FILTER, info board, ARS, ActiveRatingSystem, ACTIVE RATING, ZBRAIN, D-SPA, SP-Cache, NET FILTER, White Web, m-FILTER, m-FILTER MailFilter, m-FILTER Archive, m-FILTER Anti-Spam, m-FILTER File Scan, Mail Detox, DigitalArts@Cloud, D Alert, and related logos and icons are trademarks or registered trademarks of Digital Arts Inc. FinalCode is a registered trademark of FinalCode, Inc.