Press Release
June 23, 2021
Digital Arts Inc.
PPAP passwords can be cracked in less than a second
Ordinary computers able to crack simple passwords, facing limits to file transfer operation with passwords
Information security solution provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; Code 2326) is pleased to announce the release of an analysis report on passwords for ZIP files used in PPAP (password-protected zip file email attachments) and other applications.
The method of sending an encrypted ZIP file by email and then sending the password in a separate email (PPAP) is used by many Japanese companies and organizations. However, recently, a range of risks have been pointed out. In this article, we will be analyzing the risks of passwords. There are three primary types of passwords: PINs, login passwords, and encryption keys. PINs are used to protect smartphones and bank cards, and login passwords are entered together with login IDs to log in to web services. While PINs and login passwords can only be entered a limited number of times, encryption keys used for encrypting ZIP files etc., can be entered an unlimited number of times, as their feature.
Decrypting passwords of ZIP files that can be entered an unlimited number of times
We tried to see how long it would take to crack the password of a ZIP file using a publicly available computer and an open source password recovery software, and were able to crack the sample password "zansin," a six-digit password of lowercase English characters, in less than a second.
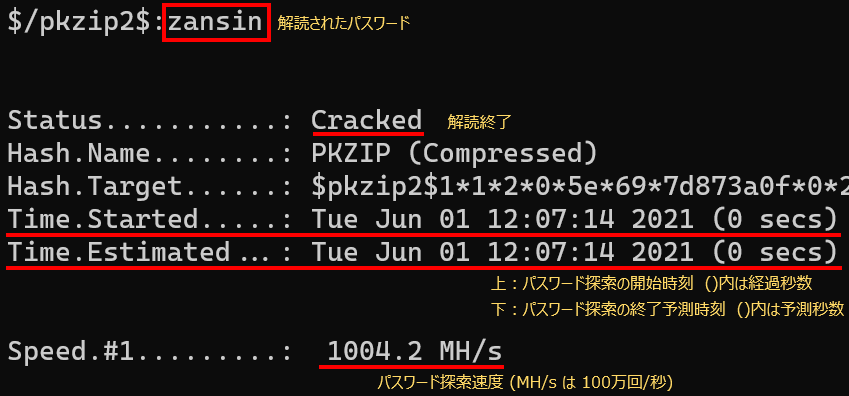
There are about 0.31 billion (26 to the 6th power) combinations of six digit lowercase English characters, and this test recorded a password search speed of about 1 billion times per second. Even with a slightly larger digits (12) of only numbers, it took only 2 minutes and 51 seconds to decode. Furthermore, not a few organizations may even operate on a standard date and time-based number password rule for their ZIP files.
As this test shows, simple ZIP file passwords can be deciphered in a short period of time by ordinary computers (*1).
| Password string | Number of characters | Character combinations | Time to decipher (*2) |
|---|---|---|---|
| zansin | 6 characters | Lowercase English characters | Less than 1 second |
| zansinzz | 8 characters | Lowercase English characters | 20 seconds |
| zansin01 | 8 characters | Lowercase English characters and numbers | 2 minutes, 13 seconds |
| Zansin01 | 8 characters | Lowercase English characters, upppercase English characters and numbers | 2 days, 6 hours (Note: maximum expected time) |
| Zans!n01 | 8 characters | Lowercase English characters, uppercase English characters, numbers and symbols (*3) | 55 days, 13 hours (Note: maximum expected time) |
| 20210601 | 8 characters | Numbers | Less than 1 second |
| 202106012045 | 12 characters | Numbers | 2 minutes, 51 seconds |
- (*1) The machine used to decode passwords was a computer available by the general public. OS: Windows 10 Pro; CPU: Core i5-10210U (4 core 8 thread); RAM: 32GB; SSD: 500GB; GPU: GTX1070 8GB RAM. A GPU is a processor mainly used for processing graphics. For processes such as password cracking, using the GPU can be multiple times faster than using the CPU. Most gaming computers have a graphics board (graphics card) and a GPU built in. For the ZIP file encryptions, we used Lhaplus, a free compression/decompression software that seems to be commonly used in Japan, with standard settings, and used the same text file for each test, only changing the password. For the decryption software, we used an open source password recovery tool, available to the public.
- (*2) Decryption was done by brute forcing the character combinations of each password. Listed is the passwords deciphered in order of length and the total time taken. Some of times list the maximum estimated time to complete deciphering.
- (*3) 33 types of "symbols" were assumed. <<space>>!"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
There are limits to operation with passwords. Alternative file transfer methods to PPAP must be considered
The incident risk of PPAP lies in both receiving and sending files. The risk when receiving files is that there may be attacks by things such as Emotet or IcedID, which exploit ZIP encrypted files to get around anti-virus software and infect computers with malware. The risk when sending is that the file may get leaked if the email is mistakenly sent to the wrong address or forwarded. It is also important to understand that passwords themselves can easily become vulnerable depending on how they are used, for example, if they contain only a simple string of characters or if they are used repeatedly.
For these reasons, Digital Arts has been sounding the alarm about the incident risks of PPAP. As an alternative file transfer operation to PPAP, we provide the email security product m-FILTER Ver. 5 and ZIP Encryption Circumvention in our product FinalCode@Cloud, both of which are primarily used by local governments, etc.
Hokkaido Government Office adopts the ZIP Encryption Circumvention software m-FILTER and FinalCode
Click here for an analysis report on ZIP file decryption
The following is available on our website.
Security Report: "One-second ZIP file decryption of 'zansin,' a password used in a popular TV show"
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995 the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere.
https://www.daj.jp/