Press Release
October 5, 2021
Digital Arts Inc.
Beware of attacks that use unfamiliar XLL files (Excel add-ins)
— The Excel add-ins that can slip through sandboxes and anti-viruses —
Information security solutions provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; hereinafter referred to as "Digital Arts"; Securities Code 2326) is pleased to announce the release of a security report on under-talked-about attacks that use XLL files (Excel add-ins).
Recently, there has been an increase in attacks using unfamiliar XLL files (Excel add-ins). Based on suspicious XLL files we obtained, we were able to investigate how the malware infected the system. A major concern with XLL files is that their behavior cannot be reproduced in a sandbox, and their detection rate by anti-viruses is low.
Attacks using unfamiliar XLL files (Excel add-ins) are on the rise
On September 2, 2021, an alert was issued on the official Japan Medical Association (JMA) website, claiming that there were suspicious e-mails circulating posing as JMA.
[Alert] Suspicious E-mails Circulating Posing As the Japan Medical Association
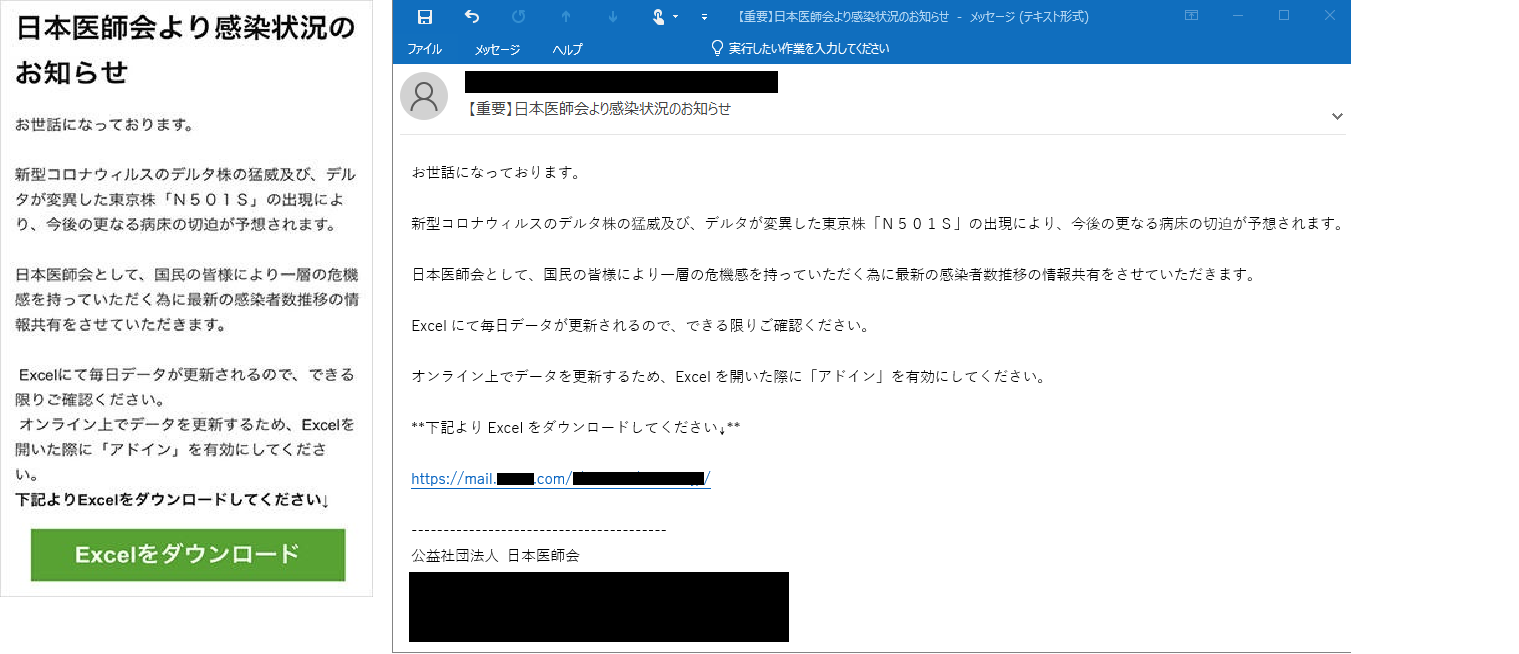
Left: An example of a suspicious e-mail posing as the Japan Medical Association (from the official website)
Right: An example of a suspicious e-mail posing as the Japan Medical Association (Note: Reproduced by us based on reported information)
Reportedly, when the link in the e-mail was clicked, an Excel file would be downloaded from the Internet. Digital Arts has obtained this suspicious Excel file. Although attacks using XLL files have been observed overseas, they have not been observed much in Japan, and there have been few warnings.
The suspicious file downloaded onto computers by the e-mail, an Excel add-in file

The file name contains an unfamiliar extension ".xll" at the end, which is an add-in file for Microsoft Excel.
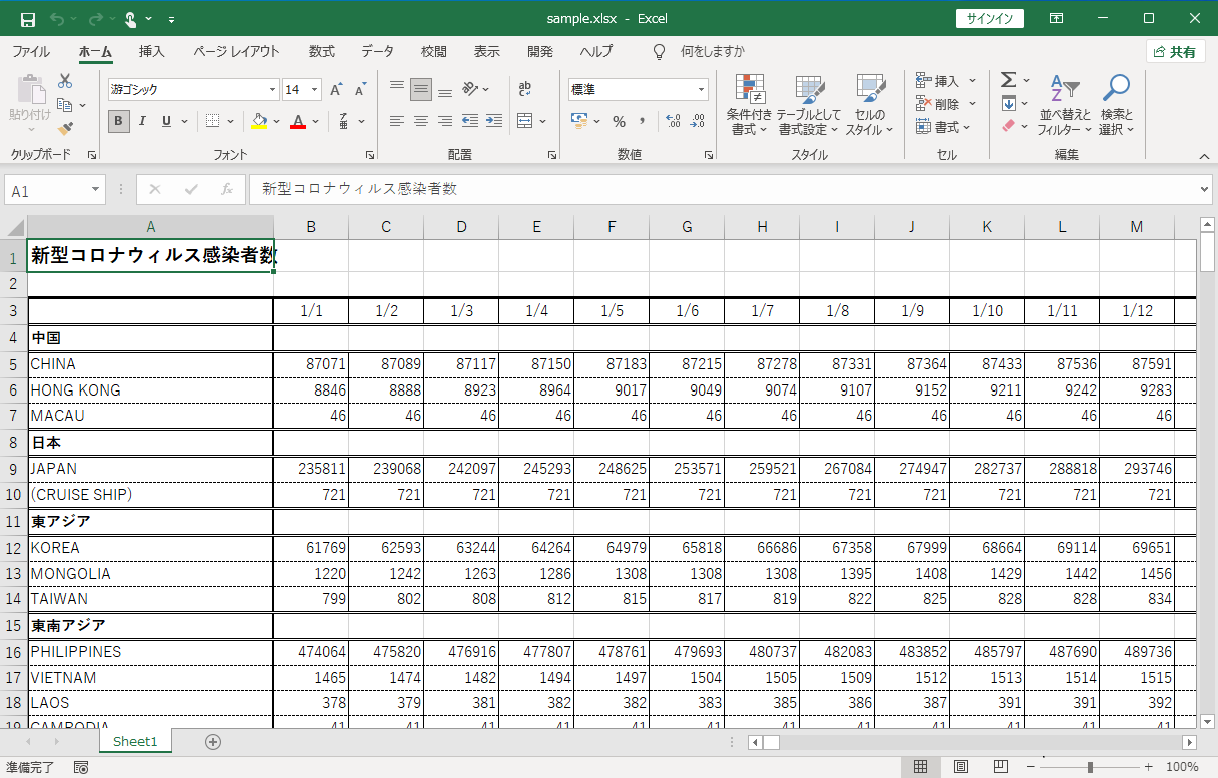
The XLL file contained malware called "Warzone RAT." RAT (Remote Administration Tool or Remote Access Trojan) is a remote control malware. The "hijacking" method can be used to steal information from the infected device or to instruct the device to perform irregular operations, thereby expanding the scope of the attack. The e-mail that tricked the Japan Medical Association in this instance was written in Japanese, and the decoy file was also created in Japanese. It is assumed that the attackers were clearly targeting Japan. D-Alert, our free cyber risk information service, has issued several reports on attacks using XLL files.
Incoming e-mails and URLs access thought to infect with the malware (Warzone RAT) have begun being detected since 27 Aug.
Incoming e-mails and URLs access thought to infect with the malware (Vidar) have begun being detected since 12 Aug.
Excel add-ins that slip through sandboxes and anti-viruses
・Behavior not reproduced in the sandbox in some cases
If the Excel installed in the sandbox is an older version, the add-in cannot run and malicious behavior cannot be detected. In addition, some sandboxes were not able to detect the malicious behavior of add-ins because they were not processed to open the XLL files in Excel, even when using newer versions of Excel.
・Low detection rate by anti-virus software
We checked using an online multi-scanning service and found that only two of the 65 anti-virus software had detected the infections. Of course, it depends on when such checks are conducted. With time, the number of software that can detect the attacks will increase as they register signatures (particular attack patterns such as malware and unauthorized access). However, it could be possible that infected e-mails had been sent before the attack patterns were registered with anti-virus software and had slipped past them undetected.
The new standard for security measures, bringing Whitelisting to you
Realize a secure world where you can open all incoming e-mails, access the websites you want, only touch information that can be safely accessed, and reduce the burden of information system departments with Whitelisting. With m-FILTER Ver. 5, when an XLL file is attached to an e-mail, it judges if the file is potentially dangerous with an "executable file" or "prohibited extension" by using the "attached file forgery judgment"countermeasure against forged e-mails, thus preventing the reception of such e-mails. i-FILTER Ver. 10 can prevent the downloading of XLL files and other dangerous files from the web with its "Download Filter" feature.
▶Digital Arts' Whitelisting: https://www.daj.jp/bs/ifmf/
▶Click here for a report on attacks using unfamiliar XLL files (Excel add-in)
The following is available on our site.
Security Report https://www.daj.jp/security_reports/211005_1/
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995, the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere.
Otemachi First Square, West Tower 14F, 1-5-1, Otemachi, Chiyoda-ku, Tokyo, Japan
URL: https://www.daj.jp/