Press Release
December 16, 2021
Digital Arts Inc.
Beware of reply-type malware attachment emails infected with "Qakbot" and other malware written in Japanese
— With the malicious characteristics of being reply emails in Japanese, there are fears the Japanese will only become more sophisticated —
Information security solutions provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; hereinafter referred to as "Digital Arts"; Securities Code 2326) is pleased to announce the release of a security report on malware delivered in suspicious reply emails written in Japanese.
On November 2, 2021, Digital Arts observed several suspicious emails. The email had two common features: a subject line that looked as if it was a reply to a Japanese email, and an attachment of a zip file containing an Excel file with macros. These are characteristics that have been found in other malware that spread in the past, such as Emotet.
Suspicious Excel files containing macros
The email that was observed had a zip file (.zip) attached to it, which is believed to contain an Excel file (.xls). The characteristics of each file name are as follows:

When you open this Excel file, you will see a sheet like the one in Figure 1.
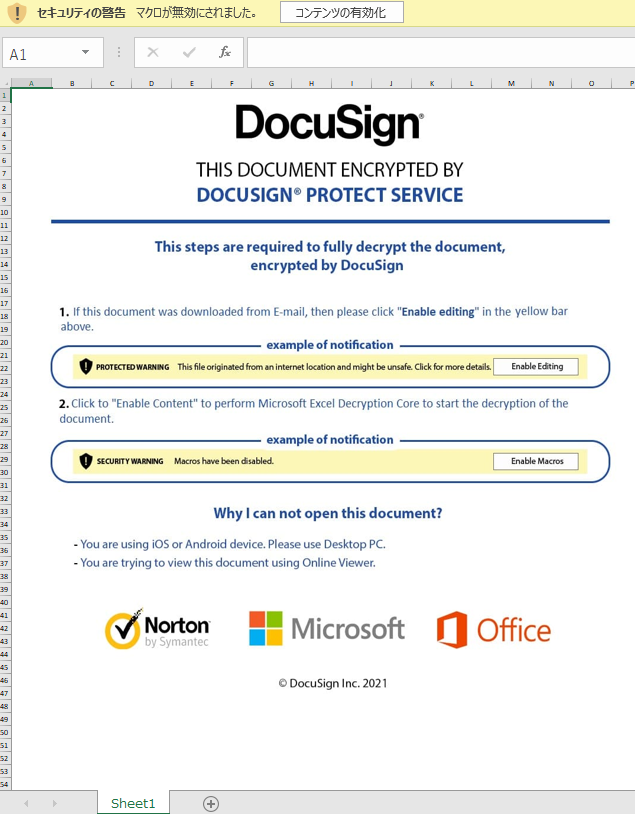
The logos and names of real companies and services are contained in the sheet, and the explanation is written as if it is being displayed for file encryption. It then instructs you to click on the button displayed at the top. However, in reality, pressing this button activates the macro and automatically executes the malicious code called the payload.
The behavior of the confirmed macro is to activate the hidden sheet and use the information contained inside to download a .dat file. When this .dat file is executed, it is believed to be infected with a malware called Qakbot.
Qakbot, also known as Qbot or Quakbot, is a malware that has existed since the 2000s. It was originally intended to steal login information for online banking and other services as a banking Trojan, but the versions that have become popular in recent years are said to have various additional features.
Troubling features of this campaign (series of activities)
The campaign (series of activities) we observed has several troubling features.
The subject of the email is in Japanese and is a reply.
We observed 29 suspicious emails of the Japanese reply type in about one day. An example of an observed email subject line is summarized below. The names of actual companies and organizations are not disclosed, but the e-mails were sent to a variety of companies in the manufacturing and insurance industries.
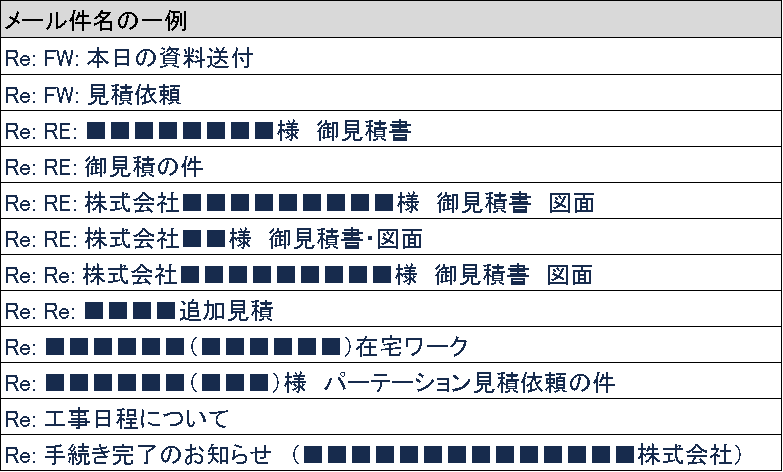
All of them have subject lines that look like they are actually being sent between companies or organizations, and at first glance, they appear to be normal emails. In particular, all the subject lines begin with "Re:", which makes it look as if the reply is from a business partner. Furthermore, there are many cases of keywords that might include attachments, such as "estimate" or "drawing," and keywords specific to the pandemic, such as "remote work" and "partitions." The attacker is likely to disguise the email as a familiar one in order to get users to open it and retrieve the Excel file from the attachment. Even if an email is written in natural Japanese, be careful not to open attachments and enable macros.
The text in Excel that prompts you to enable macros
The Excel sheet is lined with the logos and names of real companies and services, and although it is not translated into Japanese, the structure looks natural. In addition, even when macros are enabled, a popup with the logo of the OS being used is displayed, which seems to show that the attackers are specific about the appearance of their malware. The text also appears so as to make it seem like the button at the top, which activates the macro, needs to be pressed in order to view the original file. There are many cases where people who know nothing about Excel macros will read this and enable macros without thinking twice about it. Be careful not to activate macros regardless of whether the file looks okay or not. Setting the administrator not to allow the execution of macros is also an effective countermeasure.
Be wary of suspicious Japanese reply emails
In addition to the email highlighted in this press release, we have confirmed a small number of emails with attached files that may lead to Qakbot infection. There is a possibility that emails will continue to be distributed, or that the volume of emails will increase in the future. It has also been reported that Qakbot's functions include theft of files and email information from infected devices, and that it is trying to spread infection by compromising mail servers. If this kind of damage occurs in Japanese companies and organizations, it is expected that the Japanese expressions in the emails and Excel files will become more sophisticated. Emails written in Japanese and Excel file attachments containing macros have been used in other malware for some time, but we need to continue to be vigilant.
Digital Arts receives emails suspected of being infected with malware in a secure manner.
We have confirmed thattheExcel file contained in the attached zip file uses an old format (Microsoft Excel 97-2003 worksheet) and contains macros. Such files can be blocked by the old macro blocking function of m-FILTER" Ver.5. This function removes macros and scripts from Microsoft Office files, etc., which are likely to be used for malware infection by attached files, and allows you to receive emails in a secure state.
https://www.daj.jp/bs/mf/
Click here for a report on malware delivered in suspicious Japanese reply emails.
The following is available on our site.
Security Report
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995, the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere.
Otemachi First Square, West Tower 14F, 1-5-1, Otemachi, Chiyoda-ku, Tokyo, Japan
URL: https://www.daj.jp/