Press Release
February 2, 2022
Digital Arts Inc.
New Security Report on the Month Following the Return of Emotet All infections originated from e-mail, with a new app installer method also being used
Information security solutions provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; hereinafter referred to as "Digital Arts"; Securities Code 2326) is pleased to announce the release of a security report on the return of Emotet.
Emotet is a piece of malware that has been around since 2014. In addition to using conventional banking malware, Emotet has the ability to attract other malware and spread itself based on internal networks and e-mail history. Many may remember it from its rampage in late 2019 and early 2021. The outbreak ended at the end of January 2021, when the botnet used by Emotet was taken down.
However, in November of 2021, it returned. As far as we have observed, the number of Emotet-related e-mails gradually increased from the beginning of December. On December 6 and 9, we reported the observations in D-Alerts, which inform customers suspected of being infected with malware and of having their websites tampered with. In this report, we highlight the various infection methods that have been confirmed in the month following Emotet's reemergence around November 15.
Published December 6:
https://www.daj.jp/bs/d-alert/bref/?bid=172
Published December 9:
https://www.daj.jp/bs/d-alert/bref/?bid=1742
Will this resurgence cause another epidemic?
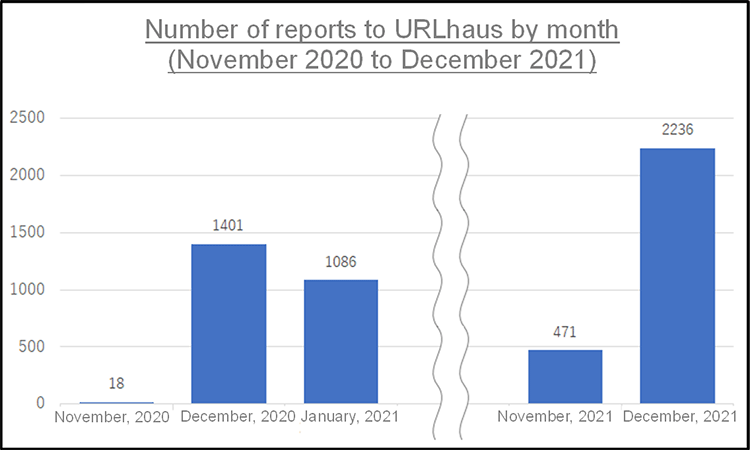
The following table shows the monthly number of URLs related to Emotet reported to Project URLhaus, which shares malicious URLs used to distribute malware, from November 2020 to December 2021. It can be seen that in December 2021 the number was high compared to just before the takedown. This is also true for the number of daily reports.
Infection methods used in the one month
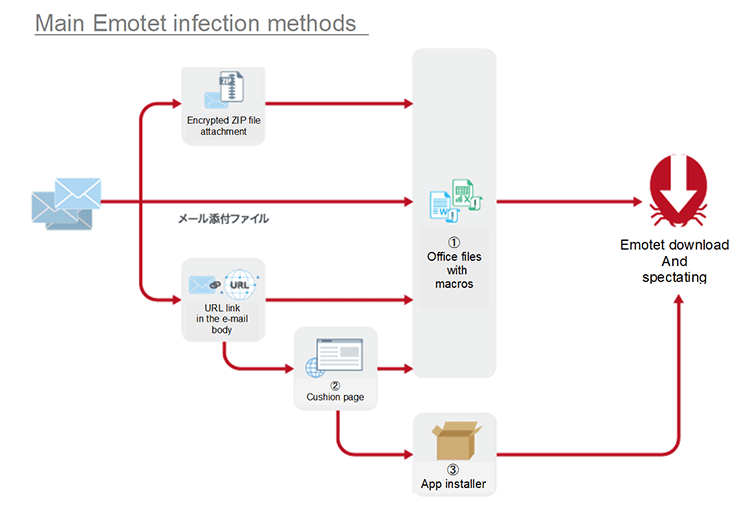
Since the reemergence of Emotet in mid-November, its infection methods changed in a short period of time, but all of the reported methods originated from e-mail.
Many of the other infection methods were due to macros contained in Microsoft Office files such as Excel and Word, a feature similar to that of the former Emotet. This time, however, there were multiple ways for the Office files to reach devices, such as in e-mail attachments, in encrypted zip files, and being downloaded from a website linked in the e-mail. Additionally, we have confirmed several cases of macros being used in Office files ourselves. Another infection method that did not use Office files was through an app installer. In this case, we confirmed that downloading and executing the app installer file (extension .appinstaller) from the link in the e-mail led to infection. Below, we will go over the methods in details.
(1) Office files containing macros
Immediately after Emotet reemerged, the most common method of infection was Office file attachments in e-mails. The most common extensions seen at this time were ".docm" and ".xlsm". These are the file types for Microsoft Word Macro-Enabled Documents and Microsoft Excel Macro-Enabled Worksheets, respectively. These files are in a file format that indicates that they were created in Microsoft Office Word 2007 or later or Microsoft Office Excel 2007 or later and that macros are enabled. Characteristics include the use of random strings of characters for variable and procedure names, and processing strings multiple times to de-obfuscate and execute them. As for obfuscation, it is relatively simple, with only unnecessary strings inserted. However, this makes it difficult to find strings that indicate execution, such as exec and start, and appears to be an attempt to circumvent security features.
(2) Cushion page URLs written in e-mails
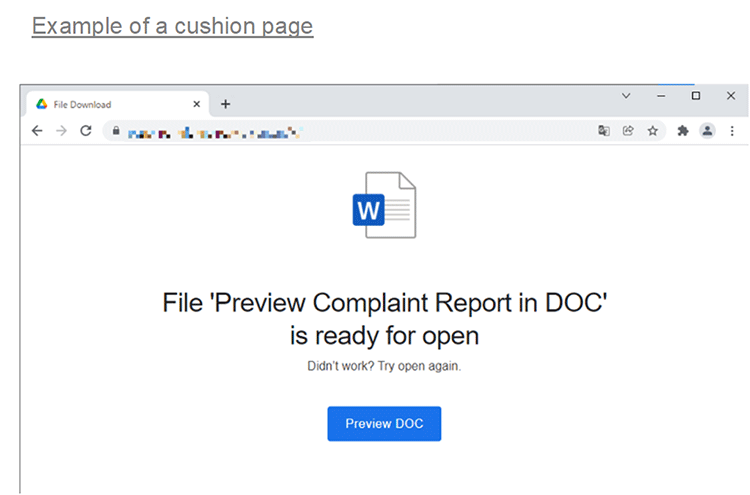
In many cases, there were no attachments in sent e-mails. In such cases, the URL is included in the e-mail, which is written to prompt accessing the URL. When actually accessed, the website includes links to download Word and Excel files containing macros. We call these sorts of URLs a cushion page. Many of the cushion pages were made from websites that had been tampered with, using vulnerabilities in WordPress and other applications. It appears as if a preview button must be pressed to view the file, and clicking on it accesses yet another tampered website that downloads an Office file containing macros. The cushion page and the page with the malicious file are both tampered websites, and in some cases, depending on how the website administrator handled the situation, have remained accessible and downloadable for several days or more.
(3) New infection method: App installers
In early December, a new infection method using app installers also emerged. An app installer is an application provided by Microsoft and made available through Windows 10. It is thought to have been included as a standard feature in many Windows 10 computers as it facilitates the installation of applications for Windows. The app installer essentially starts the installation of an application by loading the app installer file, which has the extension ".appinstaller." In the spread of Emotet, this file was also distributed from the aforementioned cushion page. The icons are identical to the normal ones and are difficult to distinguish.
Digital Arts has achieved "whitelistng" for safe use of the web and e-mail
(1) When an Office file containing macros is attached to an email
With m-FILTER Ver. 5, if a Word 97 to 2003 document (extension ".doc") or Excel 97 to 2003 file (extension ".xls") containing macros is attached to an e-mail, the old macro block feature will can block it. Microsoft Word Macro-Enabled Documents (extension ".docm") and Microsoft Excel Macro-Enabled Worksheets (extension ".xlsm") can be detected by the macro judgment feature. In addition, there is an email detoxification feature that allows attachment macro removal.
(2) If you have executed a macro in an Office file
The download filter in i-FILTER Ver. 10 can detect malicious file downloads embedded in tampered websites. There is also a control function by User-Agent for various access controls.
https://www.daj.jp/bs/i-filter/
(3) If you have accessed the download URL for the app installer
The app installer download URL identified in this case was from the *.web.core.windows.net domain. The domain itself is related to Microsoft Azure and is not all that harmful. In addition, the "*" contained various sub-domains, making it difficult to determine if only a particular domain was malicious. In order to block even such easily generated URLs, i-FILTER Ver. 10 has a feature called "whitelisting." The newly generated URLs are uncategorized and will be blocked during white operation.
Clickhere for a report on the reemerged Emotet
The following information is available on our corporate website.
Security report
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995, the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere.
Otemachi First Square, West Tower 14F, 1-5-1, Otemachi, Chiyoda-ku, Tokyo, Japan
URL: https://www.daj.jp/
- * DIGITAL ARTS, i-FILTER, i-FILTER Anti-Virus & Sandbox, i-FILTER@Cloud Anti-Virus & Sandbox, i-FILTER@Cloud D Alert Reporting Services, info board, Active Rating System, D-SPA, Anti-Virus & Sandbox for D-SPA, NET FILTER, SP-Cache, White Web, ZBRAIN, Credential Protection, White Unyo, m-FILTER, m-FILTER MailFilter, m-FILTER Archive, m-FILTER Anti-Spam, m-FILTER Anti-Virus & Sandbox, m-FILTER@Cloud Anti-Virus & Sandbox, m-FILTER@Cloud D Alert Reporting Services, m-FILTER MailAdviser, MailAdviser, m-FILTER File Scan, Mail Detox, m-FILTER EdgeMTA, EdgeMTA, FinalCode, DigitalArts@Cloud, Desk, Desk Event, StartIn, f-FILTER, D Alert, D Contents, and other related names, logos, icons and designs of our products are registered trademarks or trademarks of Digital Arts Inc.
- * Other corporate and product names are the trademarks of their respective companies.