Press Release
May 30, 2022
Digital Arts Inc.
Security Report
Beware of Emotet's New Attack Method "Shortcut Files"
— Shortcut Files Leading to Emotet Infection Are Using PowerShell and VBS —
Information security solutions provider Digital Arts Inc. (headquarters: Chiyoda-ku, Tokyo, Japan; CEO: Toshio Dogu; hereinafter referred to as “Digital Arts”; Securities Code 2326) is pleased to announce the release of a security report on Emotet.
Emotet is a piece of malware that has been known about since 2014 and was taken down in early 2021. However, it reappeared around November 2021 and has since continued to be sporadically active. Emotet infections occur when email attachments are opened and enclosed macros are triggered. However, a new attack method that uses shortcut files has been discovered.
Be aware that .lnk shortcut files are designed to remain hidden.
Around April 23, 2022, Emotet attacks using Windows shortcut files began to be observed. Shortcut file attacks have existed for some time, and have been used in targeted attack e-mails, but now Emotet has begun to incorporate shortcut files in new ways.
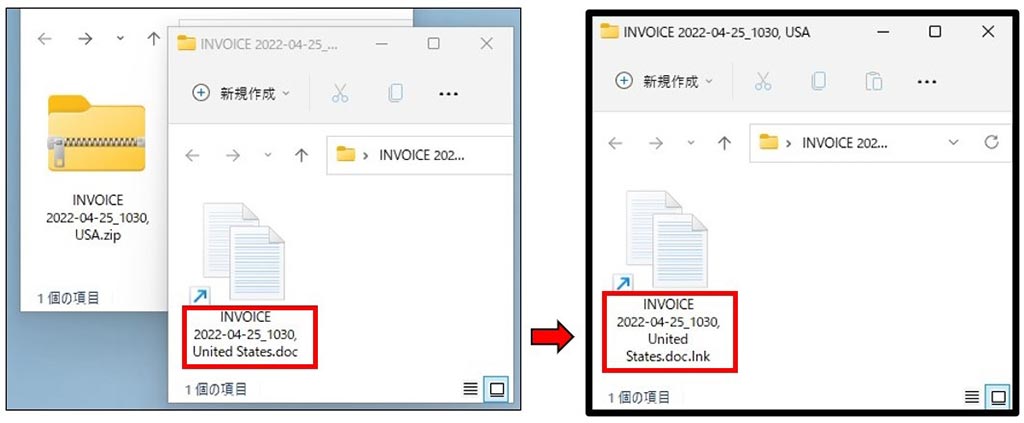
Shortcut files have the extension .lnk, which many of you may have never heard of. Even if the Windows File Explorer is set to display file extensions, the shortcut file extension .link cannot be displayed (it will display if the registry is modified). As such, as shown on the left, there is a possibility that the shortcut file will be executed, assuming that the string at the end of the file, such as doc, is the file extension.
Shortcut Files Leading to Emotet Infection Are Using PowerShell and VBS
Primarily emails are distributed with password-locked ZIP file attachments that contain shortcut files. When the enclosed shortcut file is double-clicked on a windows computer, Emotet is downloaded from the internet and infects the computer. The following behavioral patterns were observed in shortcut files.
(1) Those that use PowerShell
The shortcut file executes a command prompt. the command prompt opens PowerShell and executes a Base64-encoded PowerShell command. The PowerShell command contains information such as download URLs and attempts to access each URL until Emotet is successfully downloaded. If successful, the downloaded file is then opened by Regsvr32 and infects the computer.
(2) Those that generate vbs files and attempt to open them through WScript
From a shortcut file, the command is sent to the command prompt. The shortcut file itself has a string, and the string is retrieved with findstr, and a vbs file is generated, saved and opened. The vbs file is usually opened in WScript. Contained within is information such as download URLs. Attempts are then made to access any one of the URLs. If successful, the downloaded file is then opened by Regsvr32 and infects the computer.
Continue to be wary of Office files with macros.
The move to incorporate these methods of using shortcut files may be in response to the fact that Microsoft has implemented or will implement preventative measures against the execution of unauthorized macros in Office files, which reduces the success rate of attacks. However, it is not as clear-cut as saying Emotet will move away from using Office files. As we did not observe any emails containing Office files during the initial days following the appearance of the shortcut file method, we considered the possibility that Office files would no longer be used. However, around April 29, we began observing xls files and password-protected ZIP files that contain xls files again.
Emotet continues to cause issues around the world, with there being many reports of damage within Japan as well. Additionally, there is no denying that there are many companies that have been affected (even if they are not aware) who we simply do not know about. Through our efforts with "D-Alert," we have been contacting Japanese companies and organizations that have been infected with Emotet and become a stepping stone for the virus. We have confirmed that several hundred organizations have been infected. Attackers use a variety of methods to spread viruses, not just Emotet. We should all remain vigilant and take the proper security measures in the fight against these attacks.
Security measures proposed by Digital Arts
・m-FILTER Ver.5
Our e-mail security product, m-FILTER Ver. 5, provides e-mail filters (sending/receiving control) to prevent mistakenly sent messages, complete storage (e-mail archives) and a search function to strengthen internal control and compliance. It also promotes anti-spam and e-mail security.
m-FILTER is effective for issues such as "pThe following information is available on our corporate website.reventing attack e-mails with password-protected ZIP files," "preventing e-mails with Office file attachments with macros or suspicious files," and "preventing e-mails sent from hacked legitimate sources."
- https://www.daj.jp/bs/mf/
In addition, our new "Anti-Virus & Sandbox" option improves security by enabling the downloading and receiving of safe files from secure websites and e-mails in real-time.
- https://www.daj.jp/es/lp/avsb/
"Emotet adds a new attack method, shortcut files"
Click here for our report "Continue to be wary of Office files with macros."
The following information is available on our corporate website.
- Security report https://www.daj.jp/security_reports/220530_1/
- Be wary of Office files with macros! Emotet and xlsm files and Excel 4.0 macros
- Be wary of doc and xls files with macros being used to spread Emotet!
- File-Sharing Services Being Used by Malware
- Attacks using unfamiliar XLL files (Excel add-ins) are on the rise
- The Month Following the Return of Emotet
- Over 400 Japanese companies and organizations made virus stepping stones and sent Emotet-containing emails
- Digital Arts Inc. Overview
- Digital Arts Inc. is an information security solution provider focused on the development and sales of security software for web, e-mail, files and other uses.
Since its founding in 1995, the company philosophy has been "Contributing to a safer, better, more convenient internet lifestyle" and since developing web-filtering software to prevent the browsing of harmful information on the internet, the company has been promoting internet security products to companies, the public sector and homes everywhere
Otemachi First Square, West Tower 14F, 1-5-1, Otemachi, Chiyoda-ku, Tokyo, Japan
URL: https://www.daj.jp/